In a break from the norm, I’m going to start with a Bible reference. Romans 2:21 says:
“Thou therefore which teachest another, teachest thou not thyself?”
As a SANS Instructor this couldn’t be truer. Every time I teach a class, I am asked at least one question where I think, “huh, I’d never considered that before,” or “I really need to go look at that.” Last week I had the pleasure of teaching a group of students (mostly from Japan) about Windows forensics (see SANS FOR500) when we reached the section about historical wireless networks. At that point a student asked if we could tell if MAC address randomization was enabled. My response was, “I’m sure that information must be stored somewhere, it’s just a case of finding where and how.” I promised that I’d try to find the answer. So, while the students were working through some lab exercises, I opened Process Monitor and went to work.
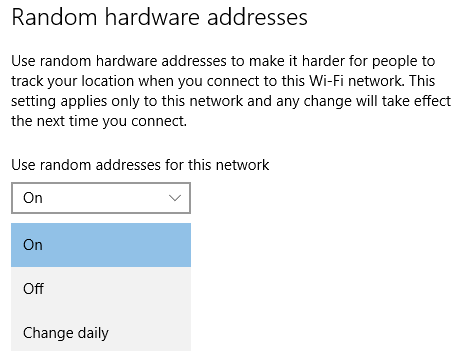
First of all, what is MAC address randomization? As you likely know, every network card has a hardware MAC address. This is a unique address by which you can connect to a network and be assigned an IP address. The randomization changes your MAC to disrupt potential snoopers from identifying the mac and model of your computer while also preventing them from tying your activity back to you specifically. There are valid privacy reasons for this, but it can clearly be used by evil-doers to avoid being caught. This is pretty simple to turn on in Windows 10/11. Go to your WiFi setting and, assuming your wireless card supports the feature, you’ll find the option as shown in the screenshot below:
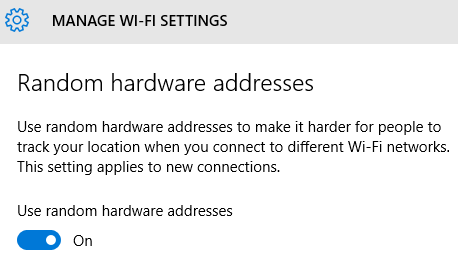
In addition to this, a user can choose to create a new MAC address for a specific network each day.
With this in mind, it might be helpful to find this information when conducting an investigation. So, where to look…
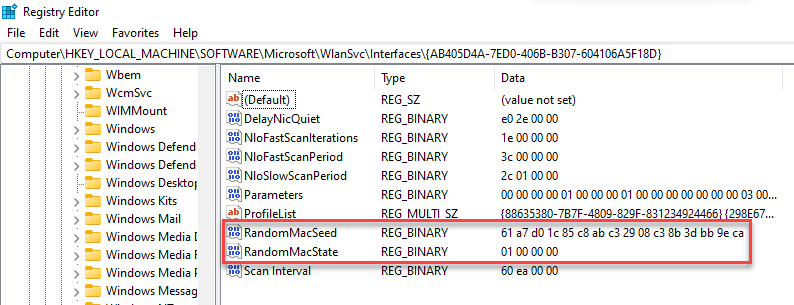
First, we’re going to dive into the registry. If a user has turned on MAC randomization two new registry values are created. These values can be found in the SOFTWARE hive under Microsoft\WlanSvc\Interfaces\<interface GUID>. The two values of interest are RandomMacState and RandomMacSeed. The former has a value of 01 00 00 00 (enabled) or 00 00 00 00 (disabled). The latter appears to be a cryptographically-generated value that is used to form the randomly generated MAC address:
The above settings are for general MAC randomization, but what about those instances where the MAC can be changed daily for specific networks? Unfortunately, I was unable to find any evidence of these changes in the Registry, but I did see settings change in the C:\ProgramData\Microsoft\Wlansvc\Profiles\Interfaces directory. If you’ve never seen this folder before, I HIGHLY recommend taking a look as it contains so much good information about wireless networks.
Once in this folder, there are sub-folders based on the interface GUID. Inside each of those folders is a list of XML files, each of those is named after the connection GUID.
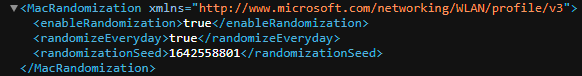
Once opened, these XML files contain a great deal of information about that specific wireless network, including the SSID, authentication/encryption method and an encrypted key that you could use to attempt to crack the passphrase. However, it also contains an entry named MacRandomization. This entry exists regardless of whether the setting is turned on or off. If it is off, the value for enableRandomization will be false. If on, it will be true along with a randomizationSeed value. If the user has also enabled the setting to change the random MAC address daily, another entry will be created named randomizationEveryday with a value of true.